
Leverage the Power of Event Tracking
Collect events and transform them into marketing and business profit
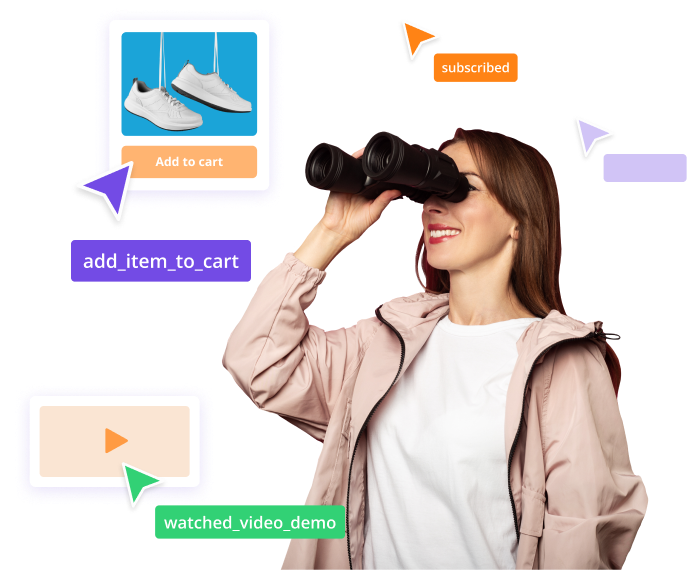
Why Do You Need to Use Event Tracking?
- With event tracking you can gain valuable insights into your customers' behavior and create targeted messages that drive engagement, retention, and revenue
What Else...
- Create personalized messages that speak directly to your customers' interests and needs
- Automate your campaigns, save time and effort while delivering more effective messages
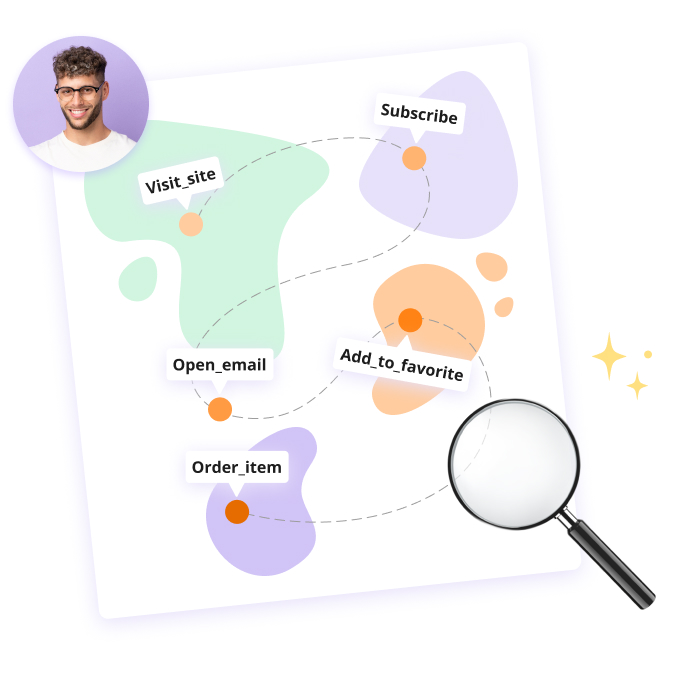



By using event tracking tools and technologies, businesses can track and analyze specific actions taken by subscribers, such as clicking on links, opening attachments, etc.
This data can then be used to create more targeted and personalized email campaigns that speak directly to subscribers' interests and needs, resulting in higher engagement, increased conversions, and ultimately, more revenue for the business.
All-in-One Tool to Market Like Pro
Find out what's working and what's not. Dig into your data to find opportunities to grow.
Get fast, 1-on-1 support and training. Access our library of tutorial videos and help guides.
Wooxy handles all things about domain authentication for clients, ensuring their emails are secure and trustworthy.
Highly scalable platform with powerful hardware and clean IP addresses. Zero tolerance to downtime.


Built for Scalability and Reliability
Wooxy apply a Role-based access control (RBAC) method
Over 5 000+ businesses all over the world trusted us









